If you are a hosting provider and you strive for giving your customers the best possible security, it’s important to know about the most common network attacks. In today’s article, I will discuss such an attack named as Distributed Denial of Service / DDoS. This attack is designed to bring an entire network’s functionality into halt.
What is a Distributed Denial of Service attack?
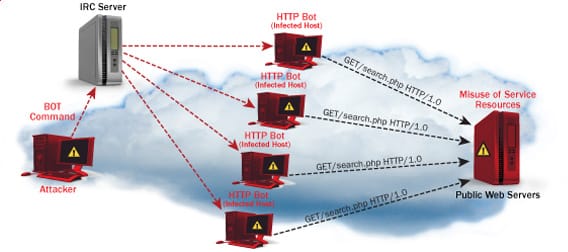
This attack is done by sending huge amount of useless or junk traffic to a specific port or server. Such high volume of traffic overwhelms the entire system and hence, even proper legitimate traffic is dropped. Distributed Denial of Service / DDoS attacks are kind of an advanced form of the basic Denial of Service attacks and have been in existence for 15 years or so. The attacks in general, start from a single source but then emerge from numerous locations all over the world.
Below, I’ll try to point out the most common types of Distributed Denial of Service attacks and how are these formed:
Fraggle: This is similar to a common type of Distributed Denial of Service attack known as Smurfing (I’ll explain it later). In this case, the attacker uses UDP echo packets at different IP broadcast addresses with a manipulated source address of the victim.
Ping Flood: Numerous ping requests are sent to the victim directly, thereby disrupting the natural service.
Bonk: This is applicable for the Windows Operating System servers and here UDP packets are sent to the DNS Port Number 53. Hence, the system gets confused and ultimately crashes down. Another similar type of Distributed Denial of Service attack is named as Boink, but, in this case, multiple ports are targeted, rather than 53 alone.
Land: Here, the culprit sends packets which are manipulated and contains the same IP address as both source and destination. This confuses the victim system and calls for a crash.
Syn Flood: This works by exploiting the three-way handshake mechanism of TCP. Here, connection requests with packets of unreachable source addresses are created aiming the victim. Hence, it is not possible for the server to complete this connection and as a result, the server tries to use most of its network resources in an attempt to acknowledge each of these requests.
Smurfing: Here, huge ICMP echo traffic is aimed to IP broadcast address, having victim’s IP as source address. Thereby, the traffic is multiplied by the number of hosts resulting system crash.
These are some of the most common types of Distributed Denial of Service attacks. If you want to add something to this list or share your thoughts, please use the comments feature below.

Leave a Reply