For business houses, a dedicated server hosting is generally more favorable. You get to control your hosting in a better way and also do proper maintenance and configuration, unlike the shared hosting services. You get a fully remote desktop and console access with dedicated server hosting, but, with that level of control, huge responsibility is also bestowed upon you.
In case of a shared hosting service, it is the duty of the hosting provider to check out all the performance and security related details of the system. However, if you are using dedicated server hosting, it’s your job to protect the dedicated server from potential online threats and also take important steps so that a security breach can be remedied.
One of the worst security breaches in case of dedicated server hosting is Denial of Service. In this article, we will try to cover that what denial of service attack is and what can be done to protect your dedicated server from this kind of security breach.
What is denial of service attack?
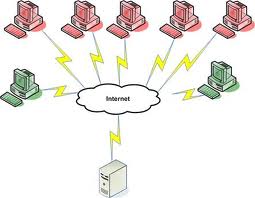
Unlike most of the other security breaches, denial of service doesn’t steal any sort of information from your server. Instead, it makes your websites hosted in the dedicated server unavailable to the users who want to access it.
A very common type of denial of service (DoS) attack is to clog the target machine with several communication requests. Hence, the target machine is not able to respond to the actual traffic and a server overload occurs. Denial of Service attacks violate all the policies of IAB’s Internet Proper Use term. In general, such attacks don’t comply with the laws of individual nations as well.
How to deal with DoS attacks?
- Choose a dedicated server that contains the best possible hardware and proper system resources.
- Make sure that the dedicated server provider has proper firewall to deal with the malicious data before it can actually reach your server.
- Make sure to check the logs all the time. If you see unexpected increase in traffic, it’s better to get cautious. If possible, locate the traffic sources and check their validity.
- You can use switches with ACL and rate-limiting capability (Routers have the same capability, but, those are easily overwhelmed by severe Dos attacks). You can even enable deep packet inspection and bogon filtering to remediate Dos attacks.
- If the Dos attacks have signatures attached, you can use Intrusion-prevention systems as well. With the granularity and processing power that an IPS has, it’s easier to analyze and block such attacks.
- You can use an Application Front End Hardware and place it on the network. Configure it in a way so that traffic has to go through this hardware before reaching the actual servers. This hardware analyzes all the data packets and then based on the priority classifies those. Finally, it determines the safe data packets to be sent to your server.

Leave a Reply